One question we’re often asked is what happens when you migrate your CipherDB App from a Free or Basic plan that uses AES-128 encryption to a Standard or Premium plan that uses AES-256 encryption. It’s a great question that highlights some of the features we built into CipherDB.
When you first register for CipherDB, we automatically create an App for you on the Free plan. You can also create additional Apps yourself using the Crypteron Dashboard. Whenever an App is created, we automatically create a default Security Partition for you that uses an encryption key tied to the App’s plan. If your App is on a Free or Basic plan, then that Security Partition as well as any new Security Partitions you add yourself, will utilize AES-128 encryption (OID: 2.16.840.1.101.3.4.1.6). If your App is on a Standard or Premium plan, the Security Partition(s) will use AES-256 encryption (OID: 2.16.840.1.101.3.4.1.46).
If you switch your App from an AES-128 plan (Free and Basic) to an AES-256 plan (Standard and Premium), or vice versa, you will have to generate a new key for that App’s Security Partition(s). You can do this by clicking on each of the App’s Security Partitions and then clicking the rollover button, shown below:
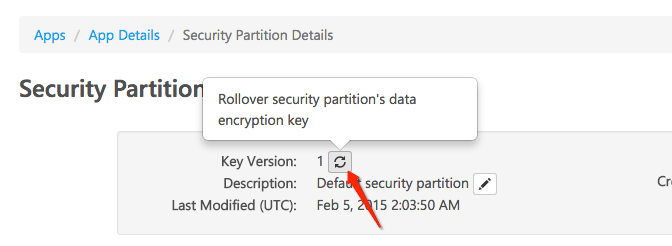
Clicking this button will generate a new Key for that Security Partition based off of the App’s current plan. If the App is on a Free or Basic plan, then the new key will use AES-128 encryption. If the App is on a Standard or Premium plan, then the new key will use AES-256 encryption. We are considering making this process automatic, so that the act of changing a plan between Free/Basic and Standard/Premium will rollover the keys for all of the App’s Security Partitions automatically. Please let us know if you would find this feature useful! After clicking the Key Rollover button, you’ll notice that the Key Version has been increased by 1. In the image above, the new Key Version would be 2.
After the Plan has been changed, and the Key has been rolled over, the final step is to restart your application or application server to ensure that it is properly synced up with the dashboard.
At this point, all new data saved by your App will be encrypted and decrypted with the new AES-256 key. All existing data will continue to use the previous version of the Key using AES-128 encryption. No code changes are required on your end. If you prefer to migrate your existing data to the new AES-256 key, you can change the migration policy, specified in the app.config file from ReadOld to MigrateOnWrite. You can read more about this feature in our updated developer guide.
As always, if you have any questions about this feature, CipherDB or any of our products, please don’t hesitate to contact us or file a support ticket!










