Your data-center is not secure. There, I said it. “But … how could you say that Sid? I’ve toured our data-center with my senior staff.” Yup. Your CISO, CIO, VP of Engineering, CTO or perhaps even with your CEO. Everyone saw burly men with guns at the entrance, iris scanners at the doors, Kevlar lined ultra-thick concrete walls, giant retractable crash barriers at vehicle entrances, ‘man trapping’ airlocks with 2 doors at opposite ends (so only one opens at a time after multi-factor authentication on each door), security cameras and more.
Humans relate well to the physical world so it’s no surprise we get lulled into a false sense of security when we see stuff like that. And guess what? Even folks at Google and Yahoo fell for this in 2013 that allowed the NSA to exploited them.
An example of complacency
The slide below shows the fatal assumption. That the Google Cloud – including the data-centers and the links – are all secure. With that assumption baked in, there were few cryptographic measures to protect against unauthorized access.
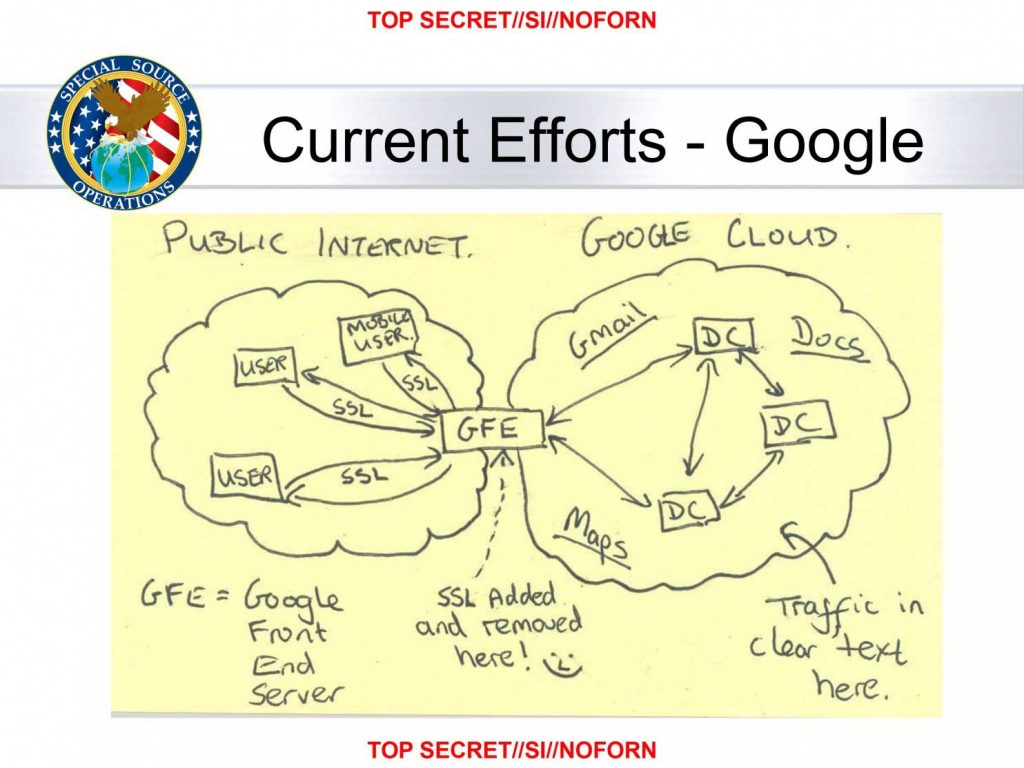
Of course, Google and Yahoo and other large giants have addressed this – but what about you? Before you answer that, I’ve got some more bad news (sorry!).
The problem has grown …
The slide above shows one very specific example: SSL removed at the front end (“SSL stripping”) to simplify the rest of the data-center application design. The problem isn’t that example. The problem is the “our data-centers are secure” mindset. Today there are even more vulnerable points than ever before. Be it malicious firmware on a router inside the data-center to an unpatched WordPress server to a vulnerable automated air-conditioning controller running an obsolete Linux 2.6.x kernel. Or Big Data which is really a Big Data Breach waiting to happen. The truth is you can’t protect against or even identify all such threats. The truth is that your data-center is just an extension of the internet and IoT wild west. It’s just housed inside a shiny building you can visit. You’ve accepted that there is no secure perimeter to your corporate intranet. So why do you really believe a secure perimeter exists for your data-center? Because … guys with guns at entrance?
The only thing that matters – protecting your data
To protect your data when you have endless vulnerabilities at the lower layers means security has to move to a higher ground. The best place for this is at the application level with self-protecting encrypted data. By doing so, you’re dramatically reducing your reliance on the lower layers, leading to greater isolation from security breaches at those lower infrastructure layers.
If it’s your customer information inside your CRM, ask the vendor how your data is self-protecting. If it’s data powering your custom-built business applications, arm your developers with the right tools. Instead of overspending on Hollywood-style data-center physical security, increase your budget for software engineering talent and software tools for security at the higher layers. You don’t have to use Crypteron (though both you and I will be happy if you did) but whatever you do – don’t go DIY. It’s downright dangerous.










