Welcome!
Thanks for volunteering to test EncryptWP, the first WordPress plugin to automatically secure sensitive user data with military-grade encryption and tamper protection. We really believe that this free plugin can be a game changer for the WordPress community, making HIPAA compliance in WordPress possible for the first time as well as bringing advanced data security to all sites that deal with sensitive data.
Features
- Automatic encryption and decryption of sensitive user fields with AES-GCM 256-bit encryption
- Support for email address encryption
- Support for all data types including arrays and objects. Any data that's compatible with the metadata API can be secured with EncryptWP.
- Searchable encryption support on exact text queries
- Bulk encryption and decryption of existing data
- Tamper protection and notification
We would love your feedback including:
- How easy is it to install and setup?
- Any performance issues?
- Are you seeing any encrypted text on the front end or within the admin dashboard?
- Are you receiving any error messages or emails?
- Does the bulk encryption / decryption time out or fail?
Table of Contents
Installation
EncryptWP will eventually be released on the WordPress plugin repository but, while it's under development, it's available to download from GitHub. For updates through the WordPress admin dashboard, install the GitHub Updater plugin.
Setup - Short Version
- Backup database
- Install EncryptWP plugin
- Go to the EncryptWP settings page within the WordPress admin dashboard.
- Copy the encryption key definitions provided to your
wp-config.phpfile. - Set Encrypt User Fields to Yes.
- Set whichever user fields and meta fields you'd like to secure to Secure or Secure + Searchable.
- Click Save Settings.
All of your sensitive user fields will be encrypted. They will then be automatically decrypted and encrypted as needed. See caveats below.
Setup - Details
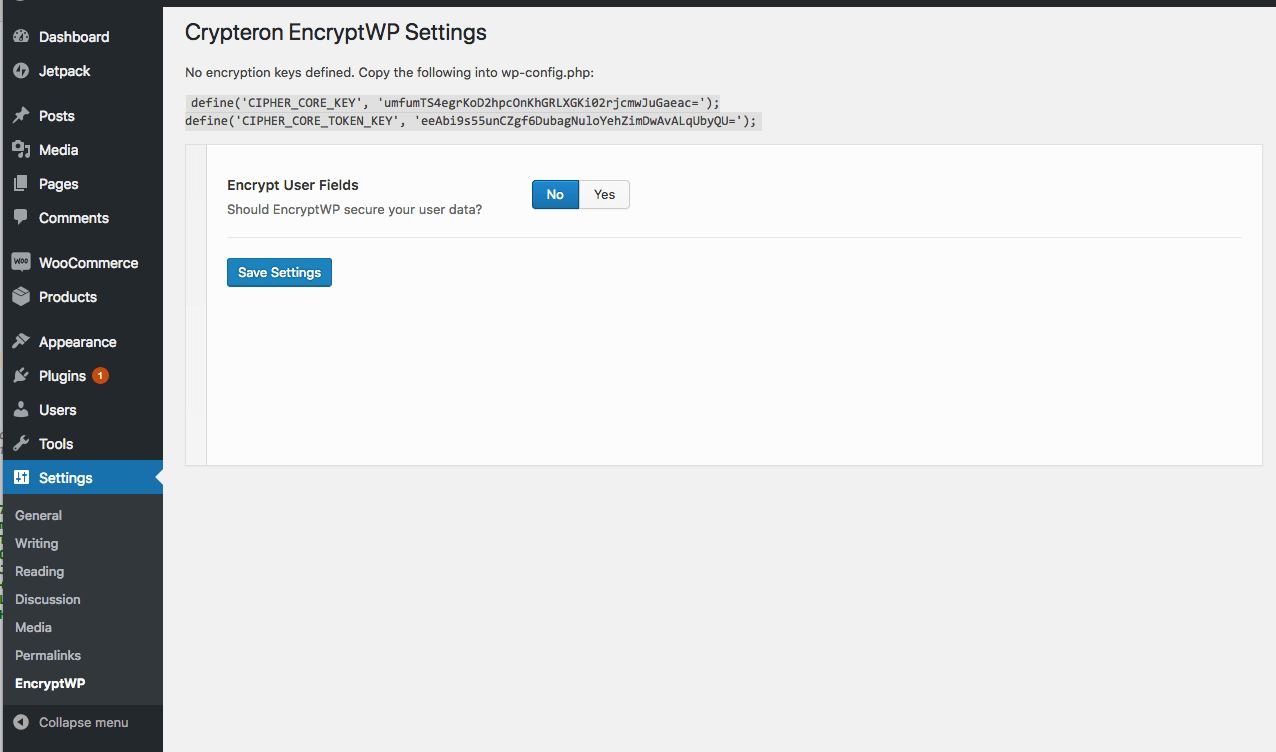
When you first open EncryptWP settings within the WordPress admin dashboard, you'll be provided with a pair of random encryption key definitions. Copy the two define statements and paste them anywhere in your wp-config.php file. See caveats below on the security of this method.
After pasting the encryption key define statements into your wp-config.php file you can refresh the page to ensure the message goes away. Next set the Encrypt User Fields toggle to Yes to expand the rest of the settings:
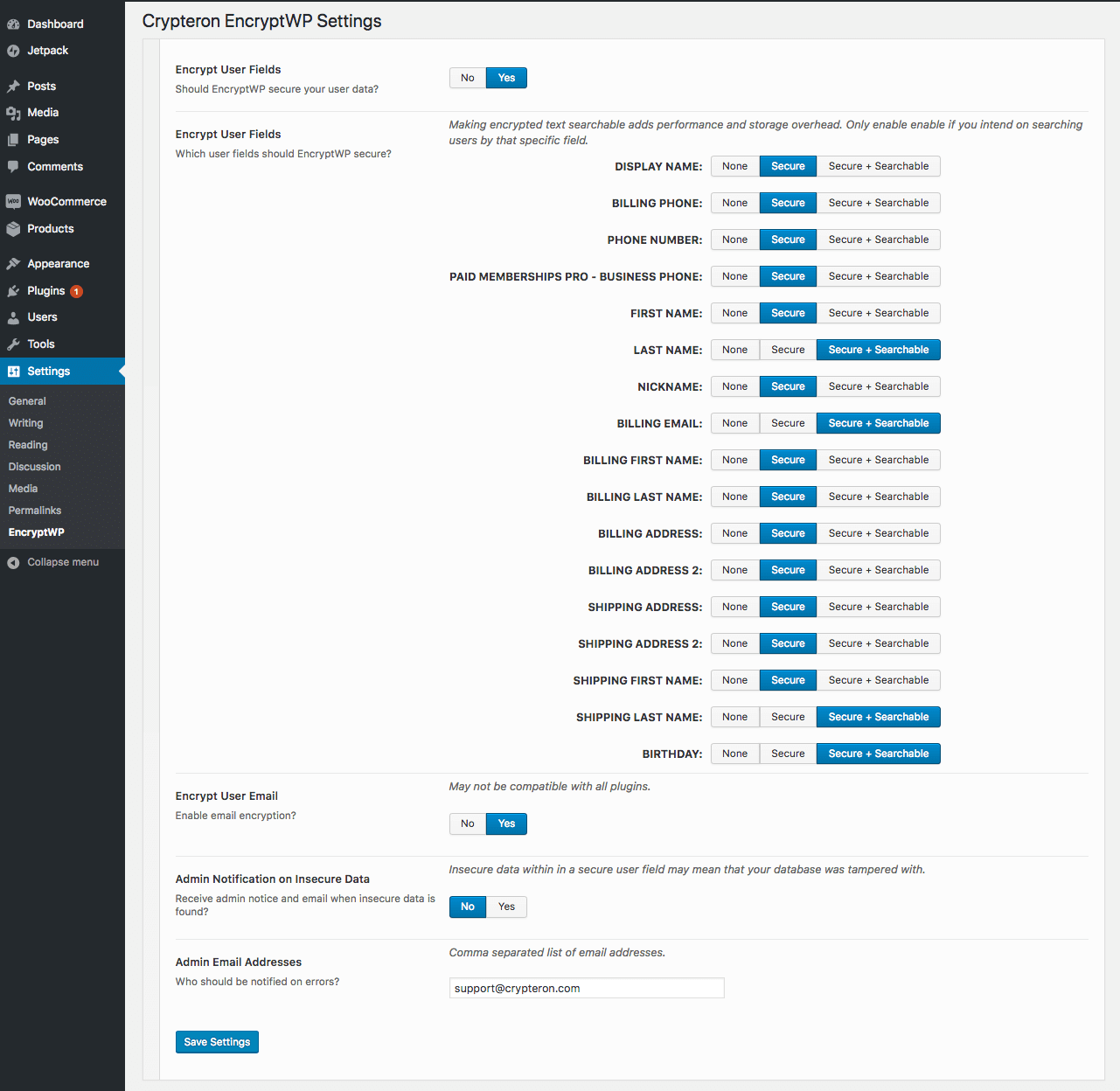
Encrypt User Fields
This panel lists all of the user fields and user meta fields that can currently be secured with EncryptWP. The list includes the native WordPress user and meta fields Display Name, First Name, Last Name and Nickname as well as the custom meta fields used by WooCommerce. In the future, we'll provide a mechanism for expanding this list via a hook or add-on API.
None | Secure | Secure + Searchable
Every field in the list has a toggle that lets you specify between security levels:
- None - no encryption is used at all.
- Secure - the field is secured with AES-256 GCM encryption which supports privacy and tamper protection.
- Secure + Searchable - In addition to encrypting the fields, a secure search prefix is added to each field allowing you to query for users with an exact text search on that field. The technical details are described below but, for now, just realize that this feature increases the size of encrypted data by a bit so only enable it if you plan on searching for users by that field.
Encrypt User Email
Email encryption is its own section because of some complexities involved. WordPress identifies users with their email addresses using the function get_user_by(). There's no hook to override this behavior so, in order to encrypt email addresses, EncryptWP overrides get_user_by() using a pluggable. This approach works so long as no other plugin tries to override the same function. The EncryptWP settings page checks to see if this function is safe to override and disables the setting if another plugin already overrides it.
Additionally, if you later install a plugin that attempts to override this function, EncryptWP will present an admin warning with the name of the incompatible plugin.
Admin Notification on Insecure Data
EncryptWP offers tamper protection in addition to data privacy. What this means is that if someone gains access to your database and replaces some encrypted text with plaintext, EncryptWP can detect and alert you of the change via an admin notice and alert email. If you prefer not to receive this warning, or are receiving too many of them, you can disable it here.
Admin Email Address
Specify a comma separated list of email addresses to receive error notifications. Defaults to WordPress admin.
Bulk encryption / decryption
After you click Save Settings, EncryptWP will perform a bulk update on all of your user data, encrypting fields that were previously in plaintext and decrypting fields that are no longer secure. This is the most complicated part of the process and has the greatest chance for error. Be sure to take a backup of your database first. We have not tested this on very large databases yet and plan on optimizing the process soon. See technical roadmap below.
Set it and forget it
EncryptWP is designed to be set up once and then left alone. Whenever a user field is requested, e.g. $user->display_name or get_user_meta($user_id, 'phone_number', true) the field will be automatically decrypted. Whenever a user is updated, those fields are automatically encrypted. It just works automagically.
Caveats
Encryption keys
This beta edition EncryptWP focuses on the flow of user data within WordPress. The next step before launching in the WordPress plugin repository is to link EncryptWP with Crypteron's powerful key management system (see technical road map below). In the meantime, EncryptWP uses a single encryption key, hard coded in wp-config.php. Please note that this is not particularly secure since that same file contains your database credentials.
Decrypting $user->display_name and $user->user_email
WordPress does not provide a hook for filtering fields fetched from the wp_users table, including $user->display_name and $user->user_email. We plan on submitting a trac request to the Core team to add such a hook. Instead, EncryptWP relies on the sanitize_user_field() method which allows us to filter these user fields so long as $user->filter is set. The problem is that$user->filter is not always set so you might see encrypted text in place of Display Name or Email. We've built a number of workarounds to prevent this from happening but, if you do find it happening, please let us know. Hopefully we'll be able to get the WordPress Core team to add a filter that fires right after data is fetched from the database.
Searchable encryption
One of the features of AES-256 GCM encryption is that you get different results every time you encrypt the same text. This protects your database from dictionary attacks. The downside to this level of protection is that you can't perform search queries over the encrypted text. After all, if you're trying to search for a user with the first name "Peter" and every time you encrypt "Peter" you get something different, then what can the database perform a match on?
EncryptWP gets around this limitation with the same searchable encryption used in our CipherDB agent library. Take a look at that blog post for the technical details. The general gist is that, whenever you search for users using a field that's set to Secure + Searchable, EncryptWP hooks into the WordPress user query system and adds a cryptographically secure search prefix. The end result is that searching for a user by one of these secure fields just works. There's nothing special you need to do.
The caveat here, though, is that this only works with exact searches. In other words if you're searching for users with the first name, "Peter", you can't type in "Pete". You have to type in "Peter" exactly as it's written. Don't worry about upper or lower case, though.
Encrypting email addresses
The wp_users table limits email addresses to 100 characters long. Unfortunately this is often not enough to store encrypted email addresses, which are considerably longer than their plaintext versions. EncryptWP gets around this limitation by storing encrypted email addresses in the wp_usermeta table instead and replacing the email addresses in wp_users with secure_[userID]@encryptwp.com where [userID] is each user's ID. All of this should be transparent to you, but if you happen to see that email pattern in the database you know what's going on.
If you find secure_[userID]@encryptwp being used visibly anywhere, please let us know.
Technical Roadmap
EncryptWP is under active development with the following features in the pipeline:
Self-hosted key vault
As mentioned above, storing encryption keys within wp-config.php is not particularly secure. We're working on a more secure storage mechanism with the keys still remaining on your web server.
Remote key management
Crypteron's data security platform stores encryption keys remotely on its own key management server. We plan on extending this functionality to EncryptWP including advanced key management features such as key rotation, security partitioning and data migration.
Enhanced bulk encryption / decryption
Currently bulk encryption and decryption happen in a single AJAX call from the EncryptWP settings panel. We plan on enhancing this process with a progress bar as well as the ability to resume an incomplete bulk operation in the event something goes wrong.
WordPress Core requests
EncryptWP would be more effective if WordPress fired a filter after loading user data from the database. This would allow us to no longer rely on the $user->filter flag, minimizing the times encrypted data is shown in the admin dashboard. We plan on making a request to the core team for such a filter.
Add-on API
We'll be releasing an Add-on API and / or a hook that other developers can call to encrypt other user meta fields.
Options data support
We plan on adding support for securing data stored in the options table.
Post data and metadata support
We plan on adding support for securing post data and metadata.