
Military-grade encryption and tamper protection for all types of data
 Crypteron secures the sensitive data in your backend applications with AES-GCM encryption. This means that your data is encrypted and signed, providing both privacy and tamper protection. Crypteron also uses row binding to detect if an encrypted value has been moved.
Crypteron secures the sensitive data in your backend applications with AES-GCM encryption. This means that your data is encrypted and signed, providing both privacy and tamper protection. Crypteron also uses row binding to detect if an encrypted value has been moved.
All data types are supported including SQL data, NoSQL objects, files, file streams, message queues and more.
Our developer SDKs support .NET, Java and Scala and take minutes to setup.
Secure structured data with object oriented encryption
When securing structured data, simply add a [Secure] attribute above each sensitive class property in C# or a @Secure annotation in Java / Scala.
Crypteron will encrypt and sign these sensitive class properties and ignore the others.


C# Example
public class Patient
{
public int Id {get; set;}
[Secure]
public string FullName {get; set;}
[Secure]
public string SocialSecurityNumber {get; set;}
}Java Example
public class Patient
{
private int Id;
@Secure
private String fullName;
@Secure
private String socialSecurityNumber;
}Automatic encryption and decryption with CipherDB when using standard data access APIs
Crypteron provides a CipherDB developer integration for all of the major .NET and Java data access libraries including Microsoft Entity Framework, NHibernate, Hibernate and Java Persistence API (JPA).
This allows us to automatically encrypt your sensitive class properties before they're persisted to the database and automatically decrypt them on the way back. No custom coding is required. It just works. Watch the demo!
Secure generic objects including NoSQL with CipherObject
Crypteron provides a CipherObject developer integration for securing objects that don't use a data access library for persistence.
This gives you the flexibility to encrypt and decrypt your objects at the ideal point in your data lifecycle. For example, you could encrypt an object right before sending it to a REST endpoint or a NoSQL data store such as MongoDB, Cassandra or Reddis.
This feature also also allows you to keep your objects encrypted in memory.
C# Example
// Secure the object before persisting
myPatient.Seal();
// Decrypt and verify the object after
myPatient.Unseal();Java Example
// Secure the object before persisting
CipherObject.seal(myPatient);
// Decrypt and verify the object after
CipherObject.unseal(myPatient);Secure files and file streams with CipherStor
Crypteron provides a CipherStor developer integration for encrypting files and file streams.
It includes support for compression and is compatible with all cloud storage providers including Amazon S3 with native support for Azure Blob Storage.
Automatic and fully integrated key management
Crypteron handles key management, without requiring any API calls on your part, so you can focus on writing great software:
- Encryption keys are encrypted with both AES256 and 521-bit elliptic curve cryptography
- Encrypted keys are stored remotely, separate from your application or your databases
- The SDK authenticates with the key management service using strong cryptography
- Keys are securely delivered to the SDK through multi-layered encryption
- Keys are intelligently cached to maximize performance
- After a key rotation, the SDK can optionally migrates data to the new key automatically and deterministically

Manage your security model from the Crypteron Dashboard
All of your Crypteron secured apps can be managed from an intuitive dashboard.
Each app can be divided into multiple security partitions, each having its own set of encryption keys.
Each security partition has a set of access control rules specifying which user roles can encrypt and decrypt data within that security partition.
For example, you can specify that doctors can encrypt and decrypt data in the medical security partition while accountants can decrypt billing data.
Respond to a data breach with a single click
The Crypteron Dashboard includes a "Pause" button that shuts down all key management operations for a specific app.
This provides a one-click response to data breaches allowing you to get a handle on the situation. You can even integrate this with any intrusion detection you already have using our REST API.
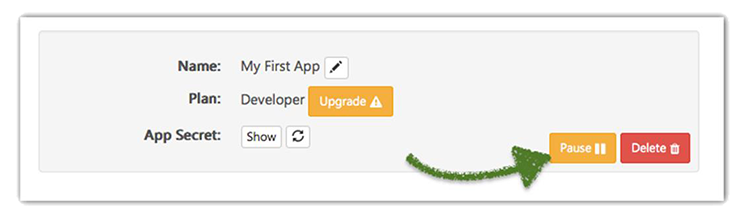
Rotate your encryption keys and migrate your data with a single a click
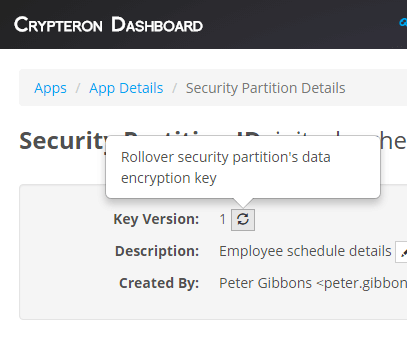 You can rotate the encryption key used by a security partition with a single click from the Crypteron Dashboard or via the REST API.
You can rotate the encryption key used by a security partition with a single click from the Crypteron Dashboard or via the REST API.
By default, the SDK will decrypt existing data using the previous encryption key and encrypt new data using the new key.
You can optionally enable a feature where the SDK will migrate old data to the new encryption key in stages.
Either option takes place transparently, requiring zero custom code.
 Crypteron provides a
Crypteron provides a  Crypteron provides a CipherObject developer integration for securing objects that don't use a data access library for persistence.
Crypteron provides a CipherObject developer integration for securing objects that don't use a data access library for persistence. Crypteron provides a
Crypteron provides a 







