SQL Injection is one of the hottest current topics in cloud data security, mostly because it is one of the hardest to stop and also the most prevalent one. So today we’ll look at how Crypteron’s database security framework, CipherDB, dramatically reduces the attack surface for SQL injection to protect your data against the #1 threat in the cloud today.
Introduction to SQL injection
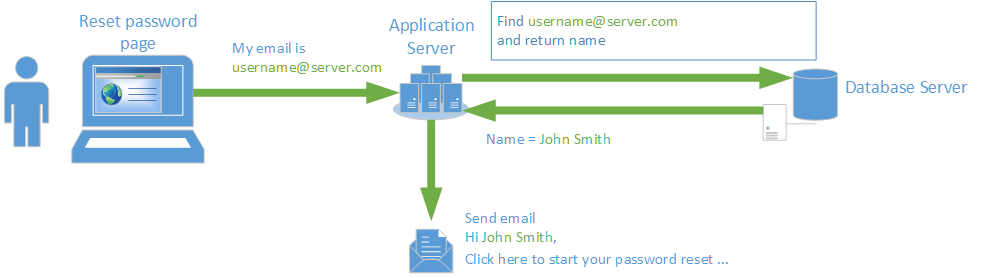
For us to understand CipherDB’s protection against SQL injection, let’s first see what SQL injection even is. Lets assume a simple scenario where a website user wants to reset his or her password. For a good user experience, we fetch their full name from the database before sending a personalized email. We’re indeed oversimplifying matters here for a wider audience but the principles are the same even in complex situations.
Programmer’s expectations
When a programmer designs that functionality, here is what he or she might have hoped to happen. A user sends an email address via an HTML form and the programmer code issues a SQL query to fetch the name. The name is retrieved and an email is sent to the user for them to continue the password reset process.
In most cases, this works and most users would use the system this way too.
Under attacker
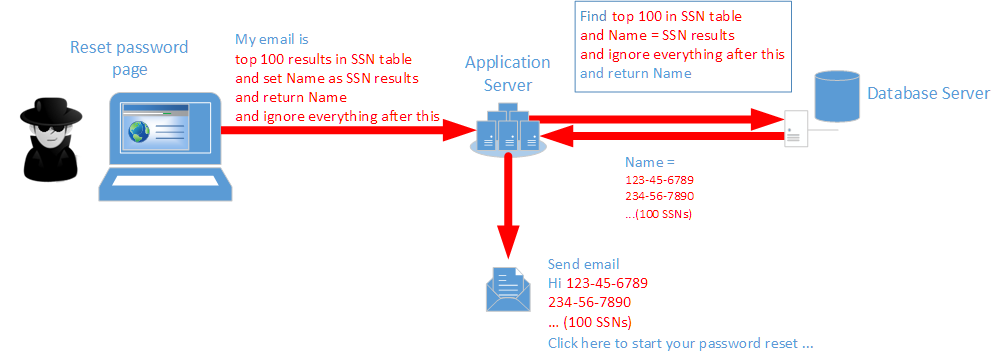
If the server code is vulnerable to SQL injection, here is what an attacker might do to breach into your data
The attacker injects new SQL logic into the HTML form and that new SQL logic now gets executed on the SQL database server. In the example above, instead of returning the Name an attacker instead asks the SQL server to dump data from another column or table (example: Social security numbers) as the “Name”. The server app then uses that “Name” and sends off an email.
What just happened? Well, you lost sensitive data and by 2014 estimates it’s going to cost you about $250 for every single record that went out! Not cheap – and worse, those cost estimates are rising each year.
CipherDB protects your data
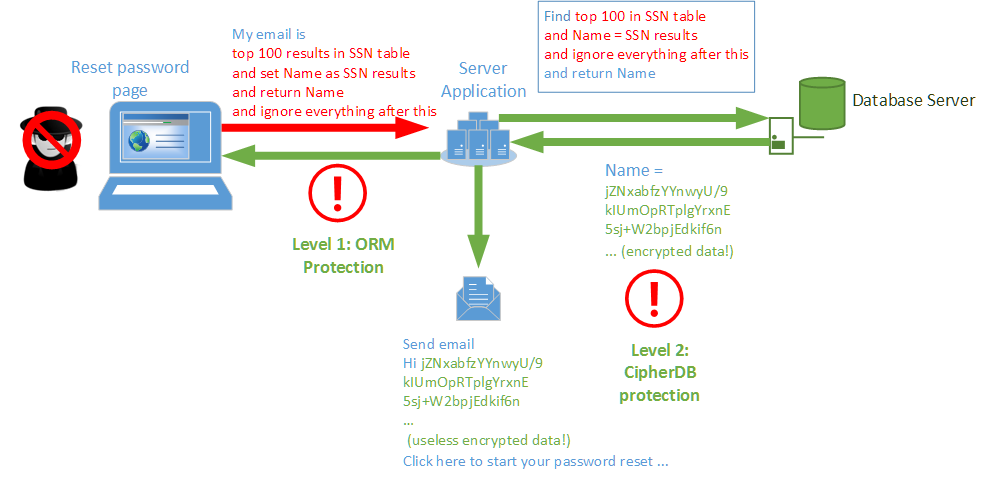
With CipherDB in place, there are two levels of protection that are shown below.
Level 1: ORM protection
The first level of protection comes from the ORM architecture which performs input sanitization. However, most ORMs (Entity Framework included) also allow programmers to voluntarily leave the regular ORM API momentarily and issue raw SQL commands or directly call T-SQL/SQL stored procedures. A programmer may use that option or an attacker may figure out a clever way to circumvent ORM sanitization or another legacy application may still be connecting to that same backend database for reporting or other reasons. If any of these were true, malicious SQL command may be injected and executed on the database server. That takes us to the next level of protection, one that’s even stronger.
Level 2: CipherDB’s strong cryptographic protection
Any data retrieved from the database at this point will be AES256 encrypted and when operating with raw SQL commands, CipherDB switches to bypass mode meaning it doesn’t attempt to decrypt the results. This means that any outgoing information is still encrypted and therefore completely useless. Effectively your data is still protected by strong, military grade cryptography thanks to CipherDB, even after an attack.
Even if somehow an attacker reaches this point and CipherDB is not in bypass mode, it’s important to note that SQL injection attacks involve substantial transformations within the SQL domain. In our above example, the attacker is returning SSNs as Names and that to a list of 100 of them concentrated together. Since CipherDB uses authenticated encryption (AES in GCM mode, per NSA Suite B cryptography) absolutely any attempt to perform such a transformation will trigger the tamper protection features resulting in a cryptographic checksum error. Zero bytes are sent out and the application is alerted via an exception. So even in such situations, your data is securely protected.
In summary, it’s fair to say that CipherDB strongly mitigates SQL injection attacks to keep your data private and secure.